Introduction
I have to say I am a little embarrassed. I actually started writing this blog over six months ago and got distracted J
Well I have just finished it off. I really think there is even more I could discuss but I need to get this out the door.
In this blog I am going to give a high-level overview of Exchange Online Protection (EOP) and discuss some major considerations as you review it.
As you learn about EOP you will find out:
- EOP is very flexible and configurable it is.
- EOP has real enterprise creditability.
- EOP is 100% integrated into the Office 365 and Exchange Online administrative and end user experience. EOP is not a bolt-on.
This is a real differentiator.
Processing Flow Chart
Before we go diving into each component, it is important to understand conceptually what the major components of EOP are:
- Connection Filtering – This enable safe listing across your entire organization. This is the first step that an email will go through as it comes into Exchange Online.
- Anti-Malware – This will always be executed. It will check the email and attachments for viruses.
- Transport Rules and Policy Filters – This is where any sort of custom policies and especially transport rules will be executed that will redirect email.
- Content Filtering – These are the anti-spam engines that analyze email coming in (plus going out).
I highly recommend review this EOP Overview - http://technet.microsoft.com/en-us/library/jj723119(v=exchg.150).aspx.
In the next few sections I will do a high-level break out on each section.
Connection Filtering
Connection filtering is user to specifically to create IP Allow and IP Block lists and to enable safe listing throughout the entire organization.
In the EAC got to Protection >> Connection Filter. There is a default connection filter policy which will be blank. You simply go add allow and block IP addresses.
There is also a checkbox called Enable Safe List. This is a list of trusted safe senders provide by third-party sources that Microsoft subscribes to. Selecting that option will skip spam filtering (content filtering) on messages sent by those senders.
Here is a quick reference - http://technet.microsoft.com/en-us/library/jj200718(v=exchg.150).aspx.
Malware Scanning
Malware is the component of EOP that checks for viruses and spyware that may be in email that is sent to your organization. Remember that viruses can infect other programs or data on your computer while spyware is gathers personal information of your computer.
Configuring Malware Policies is again simple, here is a reference - http://technet.microsoft.com/en-us/library/jj200669(v=exchg.150).aspx
First you need to go to the EAC >> Protection >> Malware Filter. This is where you can create one or more Malware Filter policies. You can prioritize the policies by using the up and down arrows. You also have the ability to enable and disable customer policies, but you can never disable the default policy.
When working with a Malware Filter policy you have several configurations that you can work with. Here is some information about the configurations you have available.
- Name and Description – pretty obvious.
- Malware Detection Response – This gives you options to delete the entire message or delete just the attachments. There are options to use the default message or to customize the message. Note that this action is applied to both inbound and outbound messages.
- Sender Notifications – this allows you define if internal and/or external senders will be notified.
- Administration Notifications – this allows you to determine which administrators should be notified for internal and/or external malware.
- Custom Notifications – this allows you to create custom notifications based on the administrator notifications that were checked earlier.
- Apply To – This is the final area which allows you to actually create criteria for the Malware Filter policy. You have the ability to assign it to user(s), group(s) and domain(s).
Policy Enforcement
Transport rules provide organizations the ability to create rules that will process inbound and outbound email. Transport rules use Predicates and Actions to create logic to process email. There are tons of actions in Transport Rules that are used for processing, data loss prevention, compliance, etc. For email hygiene there are actions such as deliver message to spam quarantine, use the following outbound connector, reject the message, delete the message, set the message header value, apply message classification, set the spam confidence level (SCL), require TLS encryption, generate incident report and sent it to, etc. There are a lot actions that you will use to create policy.
Here is a good reference to learn more about rules - http://technet.microsoft.com/en-us/library/jj919238(v=exchg.150).aspx
It is really easy to just go in and create rule using a pre-configure template or just creating a blank rule from scratch.
Content Filtering
Content Filtering is the actual component of EOP that performs the actual spam filtering based on the content of the message. You have the ability to create rules for the organization, groups of users, users and even domains.
Here is a good reference with a video showing you how to get Content Filtering set-up - http://technet.microsoft.com/en-us/library/jj200684(v=exchg.150).aspx.
First you go to the Content Filtering management area.
When setting up the Content Filtering policy the Actions screen is an important. This is where you actually create the rules that determine where spam will be directed. By default mail identified as spam is sent to the junk mail folder. There are some other options like send the email to quarantine, delete the message, add X-header, prepend subject line with text or redirect message to email address. Plus you can assign the rules based on the SCL. There are two rules, you can create one for email that is potentially spam versus email that EOP has determined to have a high confidence in spam.
This really provides organizations some real flexibility. Let’s discuss some of this.
One recommended approach is to utilize the junk mail folder and quarantine together. The nice thing about letting some potential low spam email go through to the end user is that the end user can make a decision on whether it is spam or not. With EOP, the content filtering policy will take into account the individual end user’s safe sender list. Remember in the junk mail folder the end user can indicate that an email is or is not junk mail. Those indications are remembered and then utilized when email is again sent to that individual end user. I usually say to people that there is legitimate marketing emails that are sent out that I want to be notified about. I as an end user can say email from user, domain, etc. is good email and should be routed to my inbox. While there may be other people in my organization that do not feel the same way and thus create junk mail rule that email from a user, domain, etc. should always go to their junk mail folder. End users can do this through Outlook and OWA. This really provides a level of flexibility to end users.
As you may recall I said above you can create actions for spam versus high confidence spam. If your organization really wants to make sure that high confidence spam never shows up, you can create a different action to send high confidence spam directly to the quarantine. Some organizations want to send all email to the quarantine; that is fine too. If you send email to the quarantine, you can configure the content filter policy to send notifications to end users every three days giving them the ability to release items from the quarantine. They will get an email like below.
Remember you have other actions you can take: delete the message, add X-header, prepend subject line with text or redirect message to email address. It is really up to you to come up with appropriate policies based on how your IT organization supports is end users.
You have a lot of flexibility; that is what I like so much about EOP.
Additionally part of your Filtering Policy you can create rules for international spam by looking at the languages and where the email originated from. This is huge when trying to determine what is spam and what is not. The screenshots below show the main screens where you can configure your spam policy.
Next there are advanced spam options that are available to you. Here is a good reference on this - http://technet.microsoft.com/en-us/library/jj200750(v=exchg.150).aspx. There are a ton of configurations you should consider.
- There are several rules that you turn on which will check to see if there specific html, urls, objects, etc. in the body of the message that your organization wants to categorize the email as spam.
- The SPF record: hard fail and Conditional Sender ID filtering: hard fail are should be turned on if you want extra protection again phishing.
- The Block all bulk email messages is another good option to turn on. What this will do is if there are bulk messages being sent to your organization (like a company doing a targeted campaign at your entire organization), these can be blocked. Note that end users have the ability to create their own Safe Sender lists in Outlook and OWA so if that individual wants to that email, they will still get it.
Again there are lots of good options that you can explore.
Note that you must always have a default policy. With additional content filtering policies you have the option to rules to apply them to specific to users, groups, or domains. This can be valuable if you have specific spam policy for different types of information workers.
Junk Mail Folder / Quarantine
In the previous section we talked about Content Filtering policies and how both the quarantine and junk mail folders played an important part with those policies. If you need to manage and find email in the quarantine, there is an admin screen in EOP that is easy to use. For more information, please review this - http://technet.microsoft.com/en-us/library/jj200776(v=exchg.150).aspx.
Additionally if you want to send notifications to end users that email is going to the quarantine, you need to click Enable End-User Spam Notifications on the Content Filter policy to enable this.
Additionally here is a good reference about the junk mail folder - http://office.microsoft.com/en-us/outlook-help/overview-of-the-junk-email-filter-HA102748954.aspx. The junk mail folder is also available in OWA. Remember in the content filter policies you have the ability to create rules that can direct email that potentially may be spam to an end users junk mail folder.
One side note, is that there is retention policy on the junk mail folder. I commonly have people say, I want to make sure that the junk mail folder get cleaned out. No problem. By default there is retention policy on the junk mail folder for 30 days. You can change that retention to make sure it goes away.
Finally there are way to report junk mail to Microsoft. This can be done by end users or administrators. For more information, please read this - http://technet.microsoft.com/en-us/library/jj200769(v=exchg.150).aspx.
Outbound Spam
EOP also implements rules which helps to ensure that organizations are not the originator of spam and malware. All email being sent from your organization will be checked and a policy must be present; it is not possible to turn it off. If email is identified as being spam or having malware it will either be stopped or sent to through a high risk delivery pool. All of your normal email with go through a normal delivery pool, thus not allowing your good email to be associated with email that is originating from your organization that is considered to be spam.
It is possible if a customer continues to send spam, that the email box will be stopped by Microsoft from sending email. There are notifications that can be configured to contact an administrator if this occurs. For more information, read here - http://technet.microsoft.com/en-us/library/jj200737(v=exchg.150).aspx.
Here is the screen where you can configure how to notify administrators when there is outbound spam.
Message Trace
Message Trace is another valuable feature of EOP that will allow administrators to follow messages as it passes through the Exchange Online and EOP environment. This is very helpful if you are trying to understand the rules and processing of messages. For instance, it can help you understand where good email getting stopped if you have a lot of rules. This helps the administrator to determine how they may need to re-configure or tweak EOP policies to ensure that email gets through. Additionally it is also good for understanding how email is being forwarded in a situation when you are performing an audit.
For more information read here - http://technet.microsoft.com/en-us/library/jj200668.aspx.
Connectors
Another piece is configuring Inbound and Outbound Connectors. Connectors are used to control email flow and become very important as part of an enterprise deployment.
There are two main references I recommend people to read http://technet.microsoft.com/en-us/library/jj723133(v=exchg.150).aspx and http://technet.microsoft.com/en-us/library/jj723138(v=exchg.150).aspx.
Connectors are used to create secure connections between EOP and email appliances, gateways, etc. When you are first learning about connectors, you need to understand the term “inbound” and “outbound” connectors. Neither term is aligned to “inbound” nor “outbound” email for the mail server; it is aligned to email traffic of EOP. Quicker you understand that, the more quickly this will make sense.
Let’s talk about some common scenarios I usually talk with organizations about.
- MX Record On-Premise – Many of the organizations I work with require all email to be routed through their on-premise for regulations reasons. They have appliances that must monitor both their inbound and outbound email traffic. In this scenario you would set up an Inbound Connector for EOP to receive email from on-premise and then create an Outbound Connector for EOP to send email to on-premise to subsequently be sent to out. I recommend reading Connector Scenario for Partner with Forced TLS Scenario - http://technet.microsoft.com/en-us/library/jj723154(v=exchg.150).aspx and make the appropriate configurations (for instance make an on-premise connector type). In this case, the partner is your on-premise email appliance, gateways, etc. that mail is being routed through.
- Hybrid – For hybrid with Exchange Online and on-premise, it would be the same as just described as you want to ensure your connections are secured. You will create an inbound connect to receive email from Exchange on-premise and an outbound connect to send email back to on-premise. I recommend you read both of these articles to understand the hybrid mail flow patterns: http://technet.microsoft.com/en-us/library/jj659055(v=exchg.150).aspx and http://technet.microsoft.com/en-us/library/jj659050(v=exchg.150).aspx. Then I recommend reading Connector Scenario for Partner with Forced TLS Scenario - http://technet.microsoft.com/en-us/library/jj723154(v=exchg.150).aspx and make the appropriate configurations (for instance make an on-premise connector type). In this case, the partner is your on-premise Exchange server. Actually when you use the new Hybrid Configuration Wizard, it will set up these connectors for you! For more information, read here - http://technet.microsoft.com/en-us/library/jj200790(v=exchg.150).aspx.
- Partner with Forced TLS – Used to ensure secure communication with a partner organization. Again you will create an outbound connector from EOP to the partner organization and then create an inbound connector to receive email from the partner organization. This scenario will only work if you have the MX record residing with EOP. I recommend reading Connector Scenario for Partner with Forced TLS Scenario - http://technet.microsoft.com/en-us/library/jj723154(v=exchg.150).aspx.
- Email DLP Appliance On-Premise – There are cases where organizations have DLP or other email appliance that they want to route only outbound email traffic through. The customer may be considering moving over to Exchange Online DLP solution but they need to transition over slowly. This is sometimes referred to as the Smart Host scenario. In this case the MX record resides with Exchange Online. In this case, all you need to do is setup an outbound connector to your on-premise email appliance. Please review this - http://technet.microsoft.com/en-us/library/jj723128(v=exchg.150).aspx.
- Conditional Mail Routing – Another scenario which you may set up if you have the MX record residing with EOP and you have distributed email servers on-premise. If this is the case, you may want to create multiple outbound connectors from EOP to those on-premise email servers. To support this, you will create multiple outbound connectors. Next you will create transport rules with conditional logic that will redirect the mail traffic over an outbound connector. This is actually an action you can select on a transport rule, very cool. For more information, read here - http://technet.microsoft.com/en-us/library/jj950234(v=exchg.150).aspx.
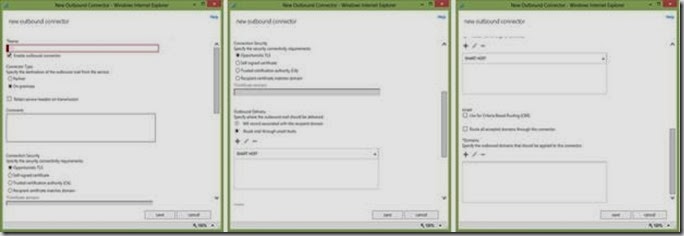
Outbound Connector
Creating an outbound connector is fairly easy. In the EAC you need to go to Mail flow >> Connectors, and then create an outbound connector. You will be presented with the following fields.
- Name – give the connector a logical name.
- Connector Type – select whether it is a partner or on-premise connector.
- Retain service headers on transmission – this checkbox should only be checked if you have an outbound connector supporting a hybrid deployment.
- Connection Security – the default is opportunistic TLS, but if you can set up certificate based connections as well.
- Outbound Delivery – will specify the location where you are sending an email to from EOP. In the case of partner scenario, you will select “MX record associated with the recipient domain”. In an on-premise scenario you will select “route mail through smart hosts” and then enter the fully qualified domain name or IP address of the destination server. If you were to enter multiple different smart hosts, EOP will randomly select the first one to send to and then uses a round-robin load balancing pattern to distribute messages across those locations.
- Use for Criteria Based Routing (CBR) – Need to check this checkbox if you plan to use the outbound connector with a transport rule as part of the Criteria Based Routing scenario described above.
- Route all accepted domains through this connector – This checkbox is used when you create an on-premise outbound connector. Checking this checkbox will not require you enter all the domains in the following field. The connector will just apply to all the domain associated to your tenant.
Inbound Connector
Next creating an inbound connector is just as easy. In the EAC you need to go to Mail flow >> Connectors, and then create an inbound connector. Here are the fields you need to fill in:
- Name – logical name for the connector.
- Connector Type – Select either partner or on-premise.
- Retain service headers on transmission - this checkbox should only be checked if you have an inbound connector supporting a hybrid deployment.
- Connectivity Security – Opportunistic and Forced TLS are your options. Pretty straight forward.
- Domain Restrictions – Select None means that there are no restrictions for incoming messages, while selecting Restrict domains by IP Address will only accept messages from specified domains where the source IP addresses are in the specified IP addresses. If you have selected Forced TLS, the Restrict Domains by Certificate option will only accept messages from specified domains where the source matches the certificate.
- Scope – You will enter the locations where we will accept email from. In a Partner scenario you will simply enter the domain you will accept email from (you can optionally enter IP addresses or accepted domains). In an on-premise type, the same really holds true, enter the domain, IP address or accepted domains. For clarification, many people ask what is the difference between a Domain versus an Accepted Domain. For a Partner Inbound Connector, the domain is the sender’s domain while the accepted domain is your domain that you want to send the email to. For a hybrid scenario, this will be set up by the Hybrid Configuration Manager. In most cases it is recommended to enter * for Domains and enter nothing for Accepted Domains. If you do not want block some on-premise domains from sending email through, you will send the same domain in both you want to allow in both domains and accepted domains.
Reports
Exchange Online Protection does have reports such as mail received, sent mail, received spam, malware detections received, malware detections sent, top malware and sent spam. It is really easy to click into these reports from the Office 365 Admin Center. You can click into an interactive dashboard as well. Here is information from the service description - http://technet.microsoft.com/en-us/library/office-365-reports.aspx.
Additionally you have the ability to download and slice through the data using additional custom filters using Excel - http://technet.microsoft.com/en-us/library/jj945734(v=exchg.150).aspx. This is really nice tool to allow you to create custom reports.
Finally if you really need to do some high end custom reporting or if you need to retain the logs for an extended period of time locally, there are web services which you can use to access all the data. Please review this - http://msdn.microsoft.com/library/office/jj984325.aspx.
Conclusions
Hopefully this will help you get started with understanding how EOP can help you and your organization protect yourself. EOP is really powerful and there is probably a lot more we can dive into in the future.




























No comments:
Post a Comment